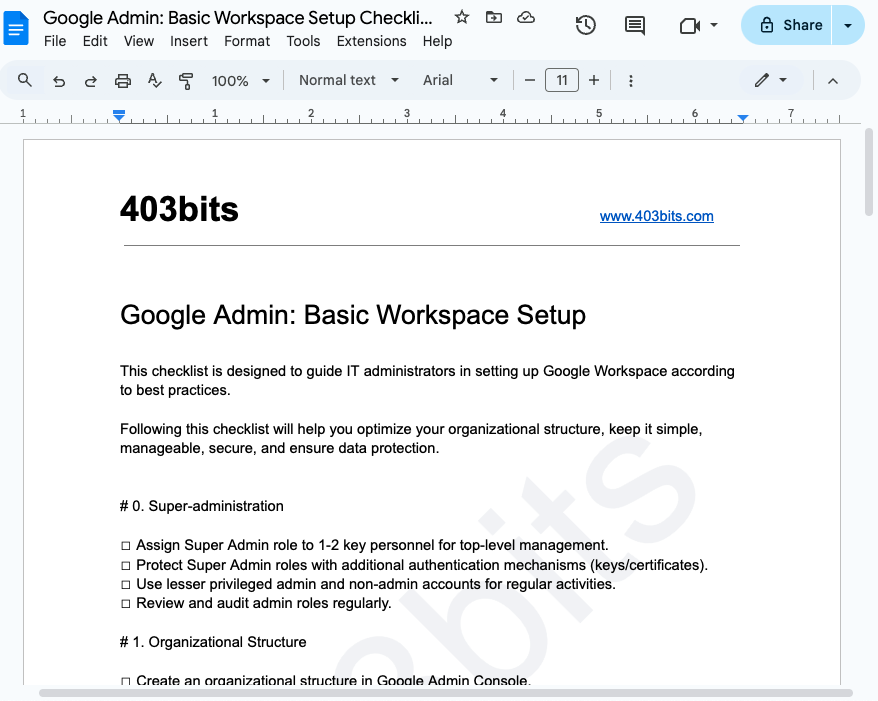
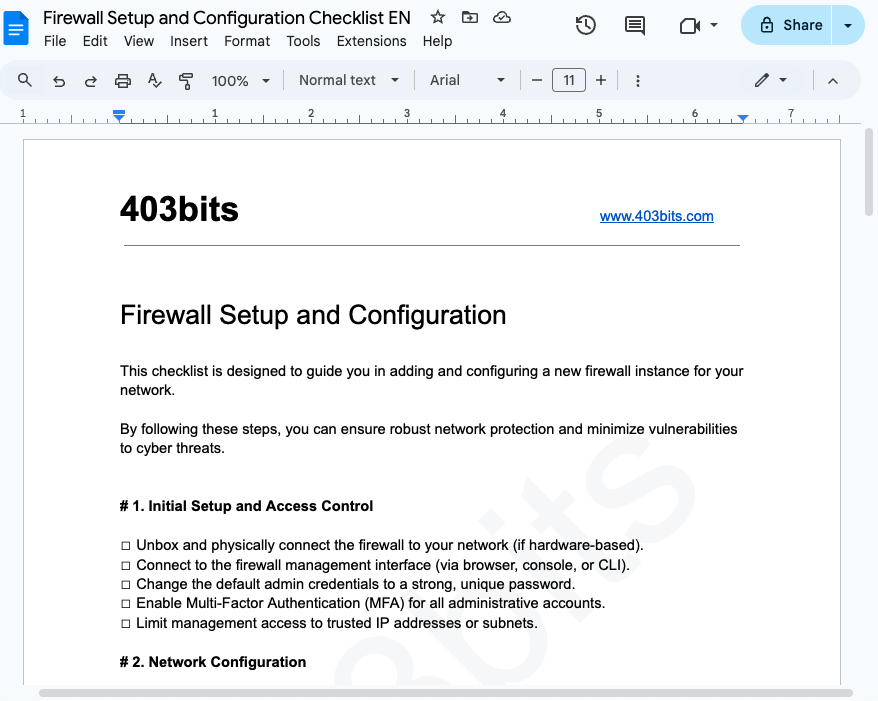
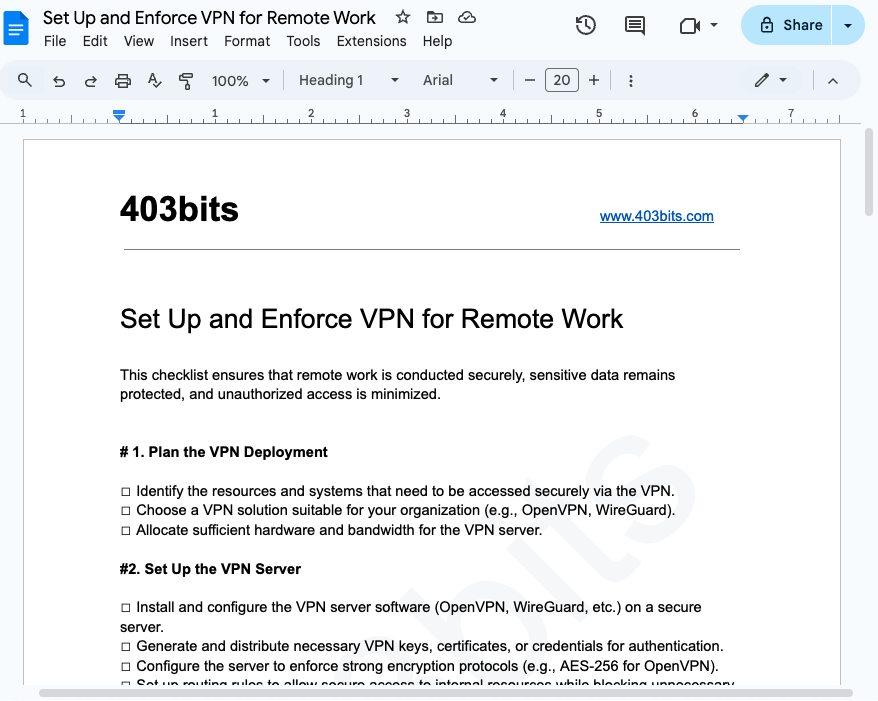
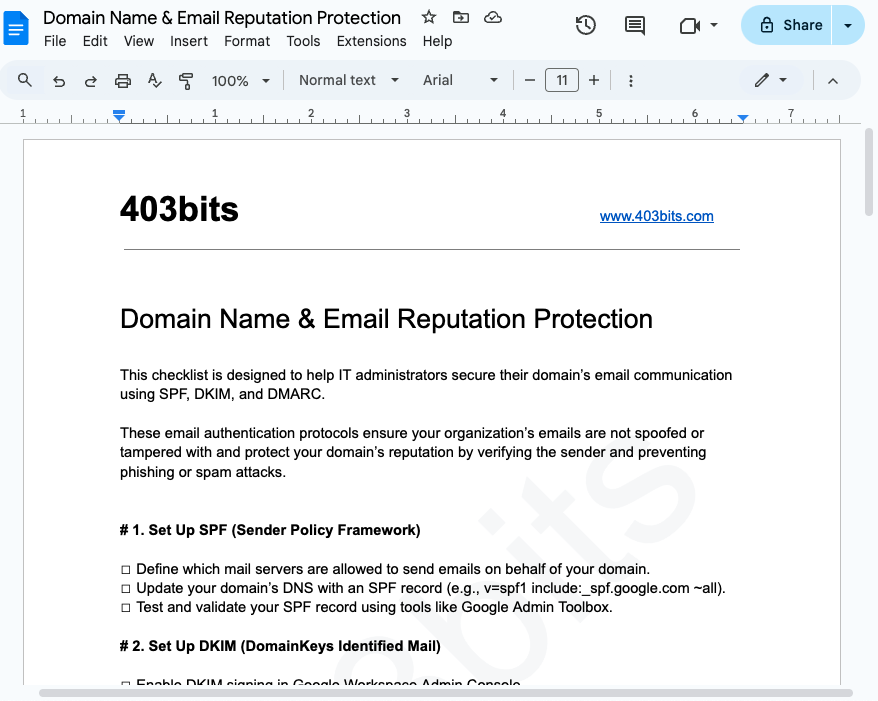
Google Admin: Basic Workspace Setup Checklist
- Super-admins
- Organizational Structure
- User Accounts, Roles and Permissions
- General Security Settings
- General Device Management
- Data Access Control
- Email and Communication Security
- Monitoring and Reporting
- Training and Awareness